SCENARIO
While technologies come and go, one constant driving force is operational technology. A fundamental shift currently happening in operational technology is the movement from core computing to edge computing. Network architects are moving as much of the core compute resources as they can to the edge of the network.
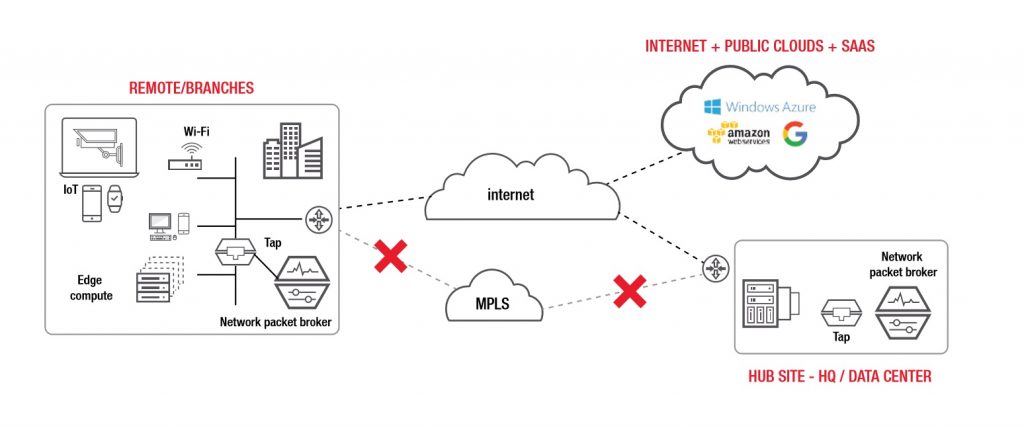
A substantial contributor to this edge computing shift is the expense of MPLS circuits, especially for the last mile to interconnect with remote offices. By contrast, internet-based network transport links can reduce remote office interconnect costs while also increasing data bandwidth with 100 MB and Gigabit Ethernet links that are readily available through ISPs.
SD-WAN services can then be layered on top of Ethernet links to guarantee performance as internet-based services can introduce latency and packet loss to the network. Cloud services can also be deployed to the edge of the network.
Security remains an important concern as the network extends further out. Inline security appliances and SSL decryption are necessary to protect against the introduction of malware into the corporate network.
IXIA SOLUTIONS
Ixia delivers the foundation of edge visibility with solutions that reduce cost, support security and optimize network performance. Ixia belongs at the heart of every edge solution.
Ixia taps allow remote devices on your network to interface with Ethernet-based links. This is the conversion point to IP. Next, NPBs take the incoming data from taps and aggregate it. Data filtration can also be implemented to reduce network, storage and compute needs.
At this point, Vision NPBs can be deployed directly path of the data allowing for inspection of data by security appliances like NGFWs and IPSs. The Ixia packet broker can also perform SSL decryption to inspect for malware.
Vision NPBs can also be used to ensure network performance and service level agreements are maintained. This is accomplished by using the Hawkeye proactive monitoring solution as a standalone application or by using an integrated version in the Vision E1S solution. This solution monitoring solution quickly and easily determines latency, loss, and jitter.
Hawkeye makes measurement simple with the largest application library in the industry; this allows users to generate many kinds of synthetic traffic to proactively monitor their live networks.
Ixia’s IxProbeTM solution combines an Ethernet tap with a Hawkeye capable end point to simplify the edge solution even further. This one device gives you complete data and performance access at the edge of your network.
