SCENARIO
News broadcasts for the last several years have shown that most enterprise networks will be hacked at some point. It is not a question of if, but when. In addition, it usually takes IT departments about 191 days to detect an intrusion, according to the 2017 Ponemon Institute Cost of Cyber Crime Study. This gives hackers plenty of time to find what they want and exfiltrate that information.
What if there was a better way? By adopting a resilient security architecture approach, the time to observance and time to remediation can be reduced. Resilience is the ability of a system to return to its original form, position, etc., after being bent, compressed, or stretched. Extrapolating this concept to a security architecture, security resilience is the ability of your architecture to recover and return to a normal state after an attack and/or breach.
A security resilience approach is about deploying functionality to:
• strengthen your capabilities to defend against attacks
• maximize your ability to rebound from an attack
• minimize the severity and cost of security breaches
IXIA SOLUTIONS
An average of 191 days before discovery and remediation is far too long to be acceptable. Ixia offers various component to make your network resilient. Here are some ways to potentially reduce that time:
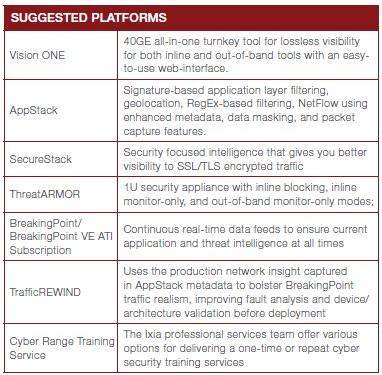
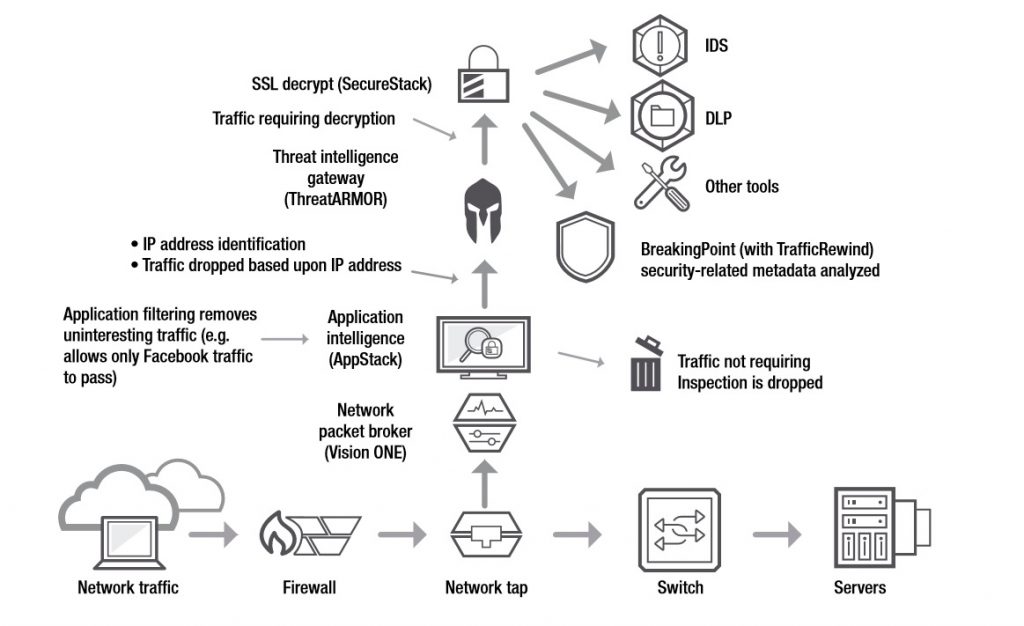
• Use the Vision ONE NPB with the AppStack application intelligence solution to find indicators of compromise
• Deploy the ThreatARMOR threat intelligence gateways to prevent the exfiltration of data to known bad IP addresses
• Decrypt SSL-based monitoring data once using the Vision ONE NPB with SecureStack, and distribute to forensic tools for faster analysis
• Implement adaptive monitoring using the automation capabilities of the Vision ONE NPB to respond to SIEM instructions, and pass suspect monitoring data to DLP tools for analysis in near real time
• Conduct cyber range training on an ongoing basis to recognize threats faster and practice responding to them properly
• Use BreakingPoint with Traffic Rewind to insert a security attack replay capability to capture security data, and view it in the lab to acquire a tactical analysis of how the breach took place
• Use BreakingPoint for threat simulation in your security lab to understand better how the threat behaves and validate that your fix stops future attacks
• Capture and filter monitoring data with the Vision ONE NPB then send that data to a purpose-built device to look at traffic patterns
• Install the Vision ONE NPB inline to support fast architectural updates and reactions to security threats