SCENARIO
Automotive technology has changed over time to a moving combination of integrated computer systems—advanced driver assistance systems (ADAS), adaptive cruise control, hybrid engines, internet access, and Bluetooth connection. To ensure the optimal design, functionality, performance, safety, security, and interoperability of these connected cars, automakers and their suppliers need comprehensive test solutions to validate devices, systems, applications, and even the entire in-vehicle network.
Automotive manufacturers have relied on complex and custom solutions to perform testing as they develop and integrate new technologies. The use of an Ethernet backbone now requires open, standard solutions that deliver testing across the whole automotive ecosystem.
Ixia’s unique automotive Ethernet test solutions include conformance, wireless, application, and security validation.
IXIA SOLUTIONS
Ixia products enable real-world validation of in-vehicle fixed, wireless, and security technologies, empowering the automotive industry to build best-in-class in-vehicle infotainment and always-on networking.
• Automotive Conformance Testing: Quickly validate the interoperability and standards compliance of the vehicle, technology that links autos and mobile devices to each other and transportation infrastructure with Ixia’s conformance test solution.
• Automotive Wireless Testing: Ensure an always-on user experience by validating connectivity within the vehicle to onboard systems, sensors, and user devices and beyond the vehicle to mobile data services and security.
• Automotive Applications Testing: Validate that multimedia applications perform optimally over any device and network by understanding how your applications and services will perform under real-world in-car conditions, attacks, and impairments.
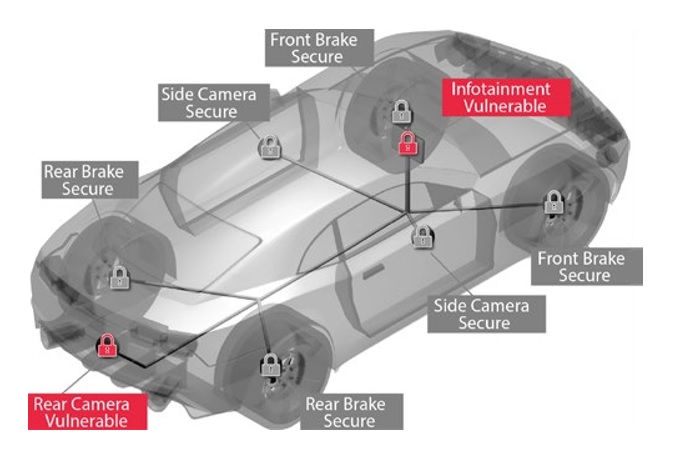
• Automotive Security Testing: Ensure the safety and security of connected cars by testing the systems designed to protect the in-vehicle network from cyberattacks. Ixia security solutions validate security capabilities using line-rate application traffic and real-world security attacks.